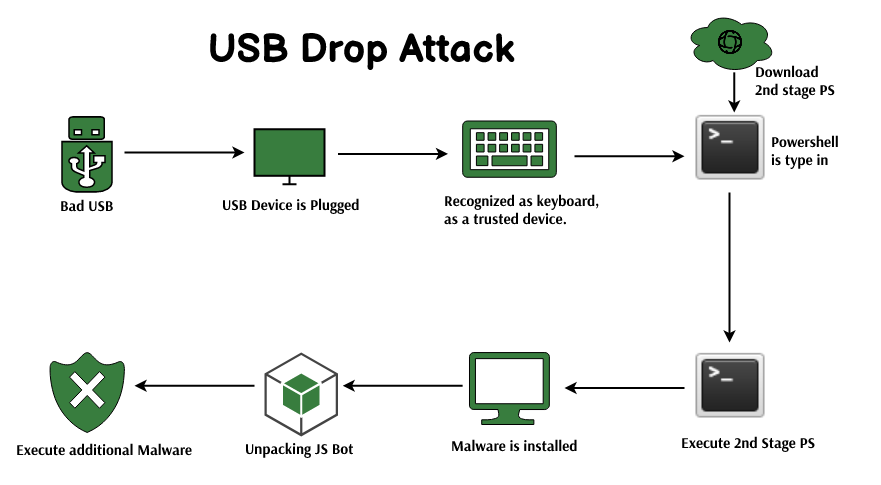
Kitsap Networking Services, Inc. - USB DROP ATTACK, what do you need to know? There has been numerous threats and hacks that have been conducted in weird and new ways, but what

The worst cyber attack in DoD history came from a USB drive found in a parking lot - We Are The Mighty

USB Continue to Threat Critical Infrastructure Security: 29 Ways to Attack Production Facility by USB