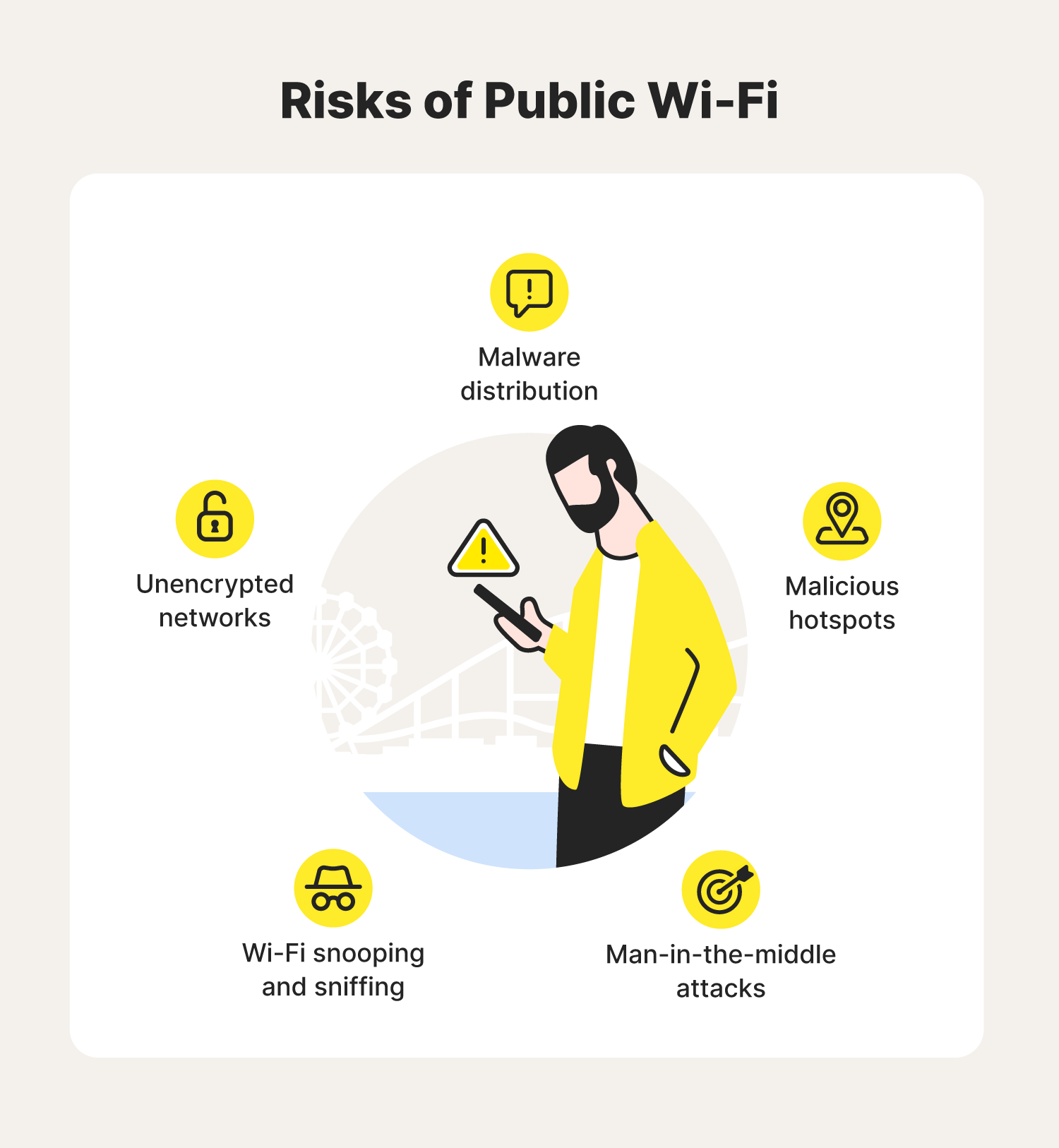
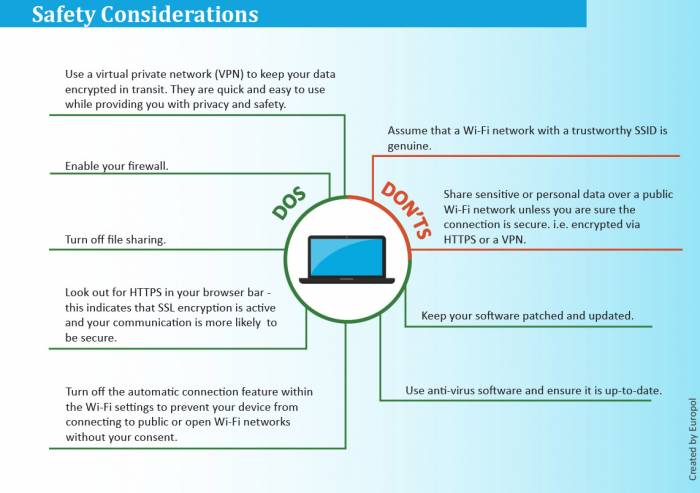
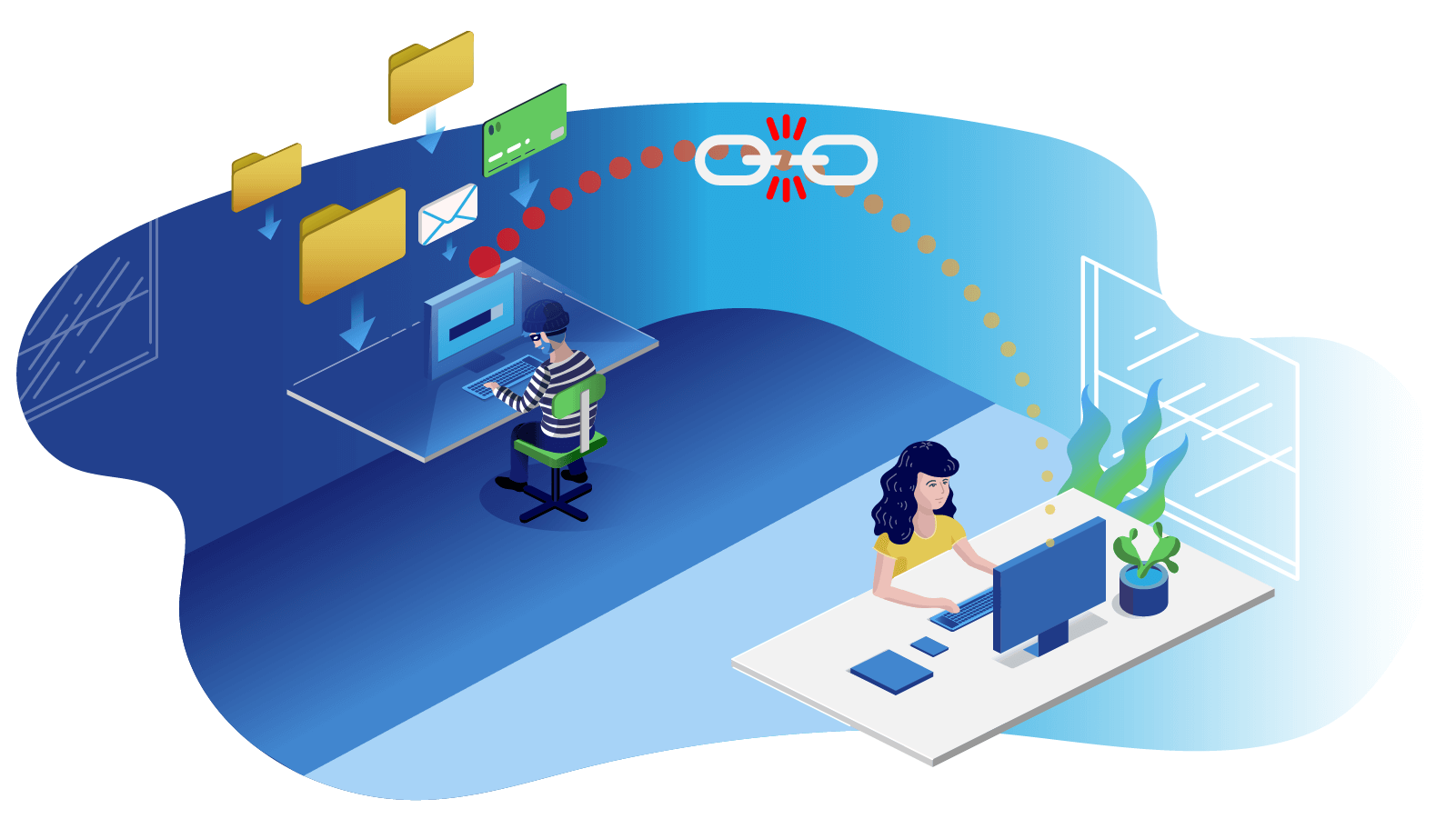
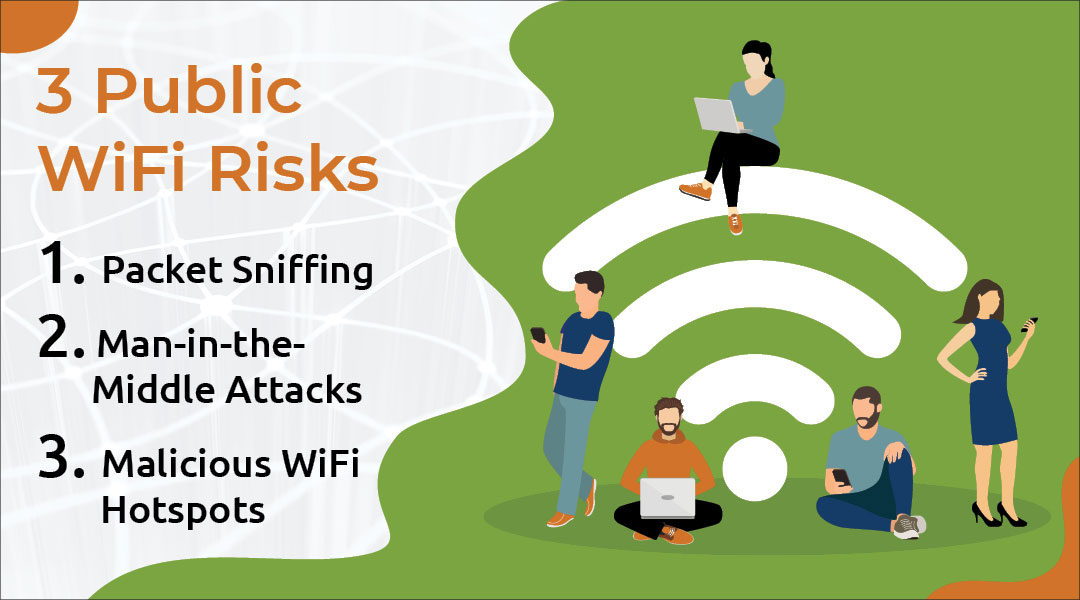
Wireless coexistence – New attack technique exploits Bluetooth, WiFi performance features for 'inter-chip privilege escalation' | The Daily Swig

Cybersecurity: Internet security 101: Six ways hackers can attack you and how to stay safe - The Economic Times